In the quickly shifting cybersecurity environment of 2025 and 2026, there is little doubt that Thejavasea.me Leaks AIO-TLP370 is a security event that has ostensibly attracted significant attention within the infosec community, development circles, and risk management teams like no other in recent memory. As a security event, Thejavasea.me Leaks AIO-TLP370 is essentially a situation that pertains to the unauthorized leakage and dissemination of what is essentially a full data package attack described by security professionals as ‘an all-in-one leak pack,’ shared from the underground repository TheJavaSea.me portal.
The implications of this particular breach go beyond the usual news headline surrounding breaches due to the nature of the breach data and the potential for misuse. Within this article, we will delve into the contents of the breach and the implications for affected entities in terms of the response and measures to fortify one’s cyber defenses against such threats.
Why the Incident Matters: The Context of thejavasea.me leaks aio-tlp370
“Thejavasea.me Leaks AIO-TLP370” represents a platform, “TheJavaSea.me,” and specifies a data set, “AIO-TLP370” – essentially implying source and contents. “TheJavaSea.me” could well turn out to be code name for an online developer group or innocuous code drop, but in cyberspace, this name is recognized and associated with data breaches, illegitimate data releases, and cracking and pirated toolkits.
Here’s a snapshot of what this leak represents:
-
AIO (All-In-One): A bundled package containing a wide variety of information and toolsets.
-
TLP370: A unique classifier that may connect back to internal or threat intelligence naming conventions.
-
Leak Context: Originally posted as a 1.2GB archive with source code, logs, scripts, credentials, and internal documents.
The combination of proprietary code, embedded secrets, and operational materials makes this leak more than a simple list of exposed passwords — it provides both attack vectors and the logic to exploit them.
How the AIO-TLP370 Leak Was Discovered
The AIO-TLP370 archive surfaced publicly around March 22, 2025, when a file titled aio-tlpfullv7.3.zip was uploaded to TheJavaSea.me. Within hours, cybersecurity monitoring services and threat intelligence researchers began flagging the leak as authentic, prompting alerts in forums, GitHub, and developer communities.
Multiple sources confirmed that the archive wasn’t a harmless code bundle — rather, it was filled with production-ready source code, cloud credentials, API tokens, logs of live activity, and internal playbooks. Because the leaked package encompassed both sensitive operational materials and reusable code, analysts treated it as a critical risk requiring immediate remediation across affected systems.
What Was Inside the AIO-TLP370 Leak?
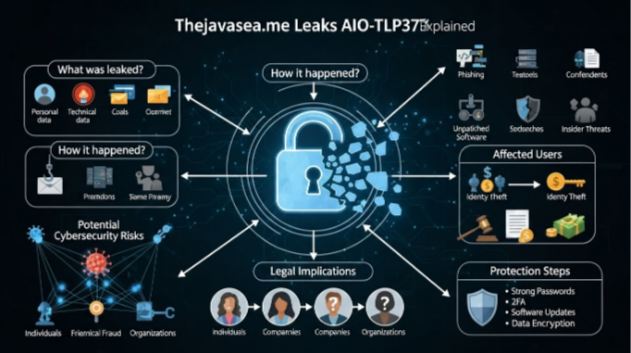
One of the most pressing questions surrounding this leak is: What exactly did AIO-TLP370 contain? Based on verified sources and cybersecurity reviews, the leak package reportedly included the following categories of data:
1. Source Code and Algorithms
The archive reportedly contained proprietary source code — including algorithms and modules that developers intended to keep confidential. This gives attackers insight into system design, potential vulnerabilities, and logical structures that would otherwise require deep reverse-engineering to deduce.
2. Configuration Files
These files often contained cloud service integration flags, API endpoints, and hardcoded credentials. Such data allows attackers to pivot into live systems or reuse the same keys in production environments.
3. Internal Documentation
Leaked runbooks, escalation procedures, and operational guidance included sequences that expose how internal teams handle incidents — a roadmap potentially exploitable during attack planning.
4. Credentials & Secrets
Perhaps the most immediately dangerous part was API tokens, SSH keys, session tokens, and other authentication materials. These can act as skeleton keys into systems if organizations fail to revoke them promptly.
5. Logs, Metadata, and Runtime Data
System logs containing IP addresses, timestamps, error traces, and user sessions are goldmines for reconnaissance — they show how systems behave under real conditions.
These contents place the leak in a higher risk category than traditional credential dumps because they empower attackers with both technical blueprints and operational shortcuts.
Who Is Affected by the Leak?
The fallout from AIO-TLP370 doesn’t just touch one sector — its implications ripple across:
thejavasea.me leaks aio-tlp370: Individuals
Personal data like emails, passwords, and logs could enable identity theft, account takeovers, credential stuffing attacks, and phishing campaigns against the users implicated.
Organizations
Businesses that used tools, libraries, or integrations related to the leaked content may see:
-
Unauthorized access to internal systems
-
Exposure to supply chain attacks
-
Reputational damage
-
Regulatory compliance issues, especially in regions governed by GDPR or CCPA equivalents.
Cybersecurity Landscape
The leak amplifies risk not only for direct victims but also for third-party vendors, partners, and service integrators whose dependencies may overlap with AIO-TLP370 components.
How the AIO-TLP370 Leak Might Have Happened
Attribution in cybersecurity is notoriously complex, but the consensus among analysts points to a few plausible vectors:
Insider Access or Privileged Leak
An individual with authorized access may have intentionally dropped the archive for personal gain, retaliation, or ideology.
thejavasea.me leaks aio-tlp370 : Supply Chain Exploit
By compromising upstream vendors or third-party developers’ systems, threat actors could have exfiltrated internal assets, then consolidated and uploaded them to TheJavaSea.me.
Configuration Mistakes and Mismanaged Repositories
Misconfigurations in cloud storage, unsecured backups, or poorly managed version control can inadvertently expose sensitive code and credentials.
Traditional Network Exploits
Methods such as SQL injection, phishing, remote code execution vulnerabilities, or stolen credentials remain go-to avenues for initial access before pivoting deeper.
SEO Keyword Spotlight: Why This Leak Is Tracked Online
The search term “Thejavasea.me leaks AIO-TLP370” has gained traction for several reasons:
-
Users worry whether their data appears in large breaches.
-
Developers seek clarification on how their code might be exposed.
-
Security teams investigate how to mitigate risk.
-
Cybercriminal communities discuss how to weaponize exposed tools.
-
Ethical hackers share prevention and detection strategies.
Building visibility around this term helps organizations chart threat intelligence policies and informs public understanding of digital risk.
Risks Associated with AIO-TLP370 — What Happens Next
Here’s a breakdown of the major threats posed by the leak:
1. Unauthorized Account Access
Leaked credentials allow attackers to take over accounts, escalate privileges, and stay undetected.
2. Infrastructure Compromise
Attackers can potentially misuse exposed API keys or cloud tokens to penetrate broader enterprise infrastructure.
3. Supply Chain or Transit Attacks
Organizations reliant on tools or codebases contained in the leak may be vulnerable due to shared libraries or dependencies.
4. Escalation of Phishing & Social Engineering
With logs and personal data exposed, attackers can craft extremely targeted and convincing campaigns.
How Organizations Should Respond: A Step-by-Step Playbook
Facing an incident like AIO-TLP370 demands speed and precision. Here’s a simple remediation checklist:
thejavasea.me leaks aio-tlp370: Audit All Secrets and Credentials
Immediately rotate all keys, tokens, certificates, and passwords that might appear or correlate to leaked contents.
Patch and Harden Systems
Update all services, apply security patches, and confirm that no unauthorized accounts or services exist.
Network Segmentation
Limit lateral movement by isolating critical systems and employing Zero Trust architectures.
Incident Detection and Monitoring
Use real-time SIEM tools to flag anomalous logins, behavior deviations, and unauthorized API calls.
User Education
Train teams on phishing recognition, secure authentication, and credential hygiene.
thejavasea.me leaks aio-tlp370: Transparency and Compliance
Notify regulatory authorities if required by law (e.g., GDPR), and communicate with stakeholders proactively.
Mitigating Personal Risk — What Individuals Can Do
-
Change passwords, especially on accounts with reused credentials.
-
Enable Multi-Factor Authentication (MFA) wherever possible.
-
Use reputable breach monitoring services like HaveIBeenPwned.
-
Avoid downloading leaked archives or visiting underground sites.
Ethical and Legal Implications
The distribution or access of leaked data in itself is fraught with legal jeopardy. The use of pirated software or leaked data could also be in violation of intellectual property acts or privacy laws.
Conclusion — The Lasting Impact of Thejavasea.me Leaks AIO-TLP370
The AIO-TLP370 leak is more than just a story in the world of cybersecurity news. The complex risk event that has occurred reveals the dangers of interconnected systems, code reuse, and weak password practices in an ever-changing threat landscape. The case study potential of the risk event has direct applications for organizations and individuals seeking to improve methods for protecting themselves in the increasingly complex world of cybersecurity threats.